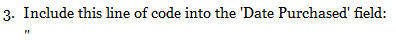
It doesn't get much more ironic than this: A ReadWriteWeb piece detailed several cross-site scripting (XSS) flaws in the McAfee Web site. The story includes some sample code that simply displays as text on ReadWriteWeb.
The New York Times picked up the story, but instead of displaying the sample code, it executed it as part of the page, causing anyone who opens the story to be redirected to the ReadWriteWeb site. The cause? An XSS vulnerability (definition), a type of Web flaw that can be targeted to steal data and otherwise ruin your day.
Here's how the mis-interpreted section in the NYT looks:
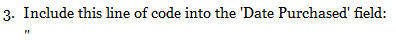
The sample code should have been displayed after the quotation, but was instead executed.
So a story about a security hole in a security company's Web site exposes the same kind of security hole in the site that's telling the story. According to Lance James of Secure Science, who figured out what was going on after being contacted by the story's author, the NYT flaw could allow anyone whose stories get syndicated with the site (or anyone who hacks a story that gets syndicated) to exploit the security hole.
The ReadWriteWeb story's author, Lidija Davis, has changed the original piece to use a screen shot instead of text, but the NYT site was still showing the original story when I just checked. Here's the updated story on RWW, and the syndicated version on the New York Times, which will redirect you to RWW. If you're fast on the draw, you may be able to hit the stop button on your browser before they NYT redirects you.
The problem lies with the sample code displayed under #3 in the "How To: HTML Injection" section of the story, according to James. He says he let the NYT know about the site problem.