McAfee, widely recognized as one of the leading providers of online security software for both home and business, appears to be struggling to secure its own Web sites, which at the time of writing this post, allow anyone with enough tech savvy to covertly do whatever they want on, and with, the site.
During tests this weekend, we discovered the company who claims to "keep you safe from identity theft, credit card fraud, spyware, spam, viruses and online scams," has several cross-site scripting (XSS) vulnerabilities and provides the bad guys with a brilliant - albeit ironic - launching pad from which to unleash their attacks.
It can't get much worse than this. This is not "yet another embarrassing incident on the Web;" not by a long shot.
Lance James, co-founder of Secure Science Corporation and author of Phishing Exposed, noted that when a criminal locates an XSS vulnerability within a well-known Anti-Virus site, it only makes the attack more effective. "It generates misplaced trust (being that computer users trust AV companies) and is paradise for miscreants involved in Scareware (Rogue Anti-Virus) distribution, as they can infect a legit copy of MacAfee's product and distribute it under their name." James said. "A win for the bad guys through the power of branding; a major loss of trust for McAfee," he added.
Not only do security vulnerabilities harm a company's brand, they can also ultimately harm its bottom line, particularly when the company in point has made millions from the software it produces to protect you online; this will surely injure the McAfee brand.
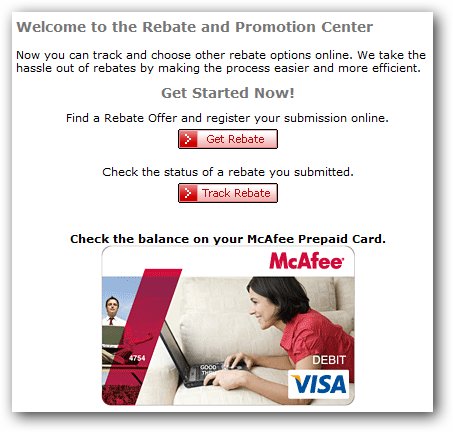
It all began when we came across a post that described some of the issues facing McAfee. Very quickly, we realized the potential for phishing on one of McAfee's sites, the McAfee Rebate Center, which allows you to inject HTML code into one of the fields it provides on its site.
If you've never seen an HTML injection in action, try this out, it's an interesting experiment.

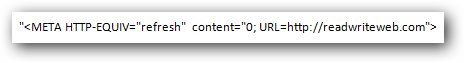
This is a very basic redirect that will take you to ReadWriteWeb.
And voila - you've just effected your first HTML injection.
Although our example is extremely simple; a no-brainer for clever coders, it illustrates a significant and more sinister point: McAfee is clearly vulnerable to XSS attacks. Much like the recent Mikeey worm on Twitter, this XSS issue is a result of poor output filtering. And while Twitter can be forgiven for not laying down the correct foundation in the beginning, the same cannot be said of McAfee, which has built its entire business around its knowledge and expertise in the field of information security.
And it gets worse. McAfee has a product called McAfee Secure which helps corporations determine whether their sites are open to malicious attack. The way it works is that sites participating in the McAfee Secure program are checked daily, and if they pass muster, they receive a McAfee Secure badge which is branded with the day of testing.
Unfortunately, it appears McAfee either doesn't run McAfee Secure across all of its sites, or if it does, the product is missing the bleeding obvious.
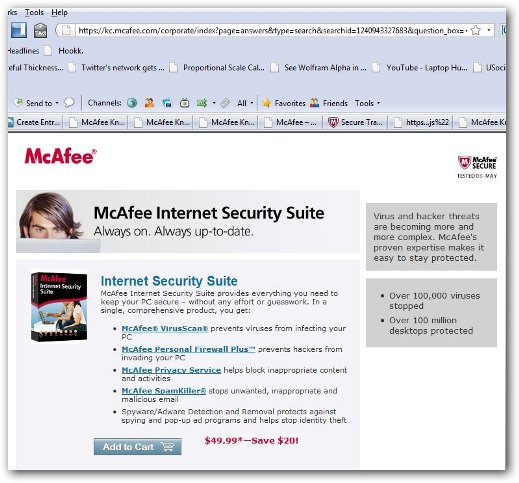
From the https, to the McAfee domain, this phish site that James created even includes a valid and dated McAfee Secure certificate.
To demonstrate how easily the exploit can be used, James created a phishing site to give ReadWriteWeb readers a real-time example. Go ahead, follow this link, and click on the "add to cart" button (we promise it won't hurt you).
What you are seeing is a cross-site scripting exploit in action. "Imagine," James said, "just how easy it would be to exploit home computers with Trojans that cause harm or steal information." A phishing site, like the one he created, could easily ask you to click a link for more information. "Or," he said, "imagine the e-mail: 'you're eligible for a McAfee rebate on your products, just click here!'" "Basically, the main use I see it for is to spread malware as McAfee."
What he's describing is ominous. The bad guys can create a modified version of a McAfee product or a bogus McAfee update that installs a Trojan, or whatever they like, and it arrives on your home machine, special delivery. You'd never know.
In creating the fake site, James points out that he didn't need to spoof the McAfee Secure logo. "We're using their certificate to validate our attack," he said.
Go ahead. Look up at the URL on the phishing site. See that https://?
Secure right?
Note: We've created a screencast (embedded below) of the redirection exploit for when McAfee fixes this; we hope it's soon.
Update May 5, 2009
It appears the vulnerability on McAfee's rebate site has been fixed; however, the test phishing site is still going strong. James gave us an update: My assumption is that remote referrers are blocking it based on firewall rules but a refresh locally shows it's still vulnerable. An attacker can simply do a meta refresh to redirect to it since that scrubs referrers.