Shortly after the LIGATT / Evans saga became more prominant in security circles, Chris John Riley of the Euro Trash Security Podcast called Greg Evans on June 16, 2010, to arrange an interview for the next podcast. He gave his real name to the person who answered the phone and to Evans, as well as briefly described the show he represented. Riley wanted Evans to talk about the recent book plagiarism accusations among other topics. Greg talked with Riley for a while outlining his thoughts, and agreed to talk the next day. While speaking with his secretary, Riley gave her the URL to his blog and exchanged SkypeIDs (Evans uses ligattsecurity).
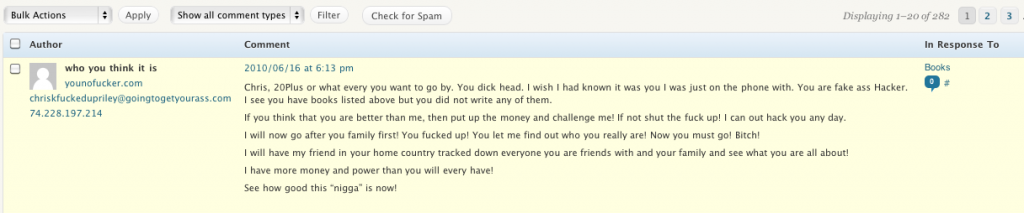
Not even 15 minutes later, a comment was posted to Riley's blog under the "Books" section:

The full text of the comment, written by "who you think it is" / younofucker.com, chriskfuckedupriley@goingtogetyourass.com / 74.228.197.214 reads:
Chris, 20Plus or what every you want to go by. You dick head. I wish I had known it was you I was just on the phone with. You are fake ass Hacker. I see you have books listed above but you did not write any of them.
If you think that you are better than me, then put up the money and challenge me! If not shut the fuck up! I can out hack you any day.
I will now go after you family first! You fucked up! You let me find out who you really are! Now you must go! Bitch!
I will have my friend in your home country tracked down everyone you are friends with and your family and see what you are all about!
I have more money and power than you will every have!
See how good this "nigga" is now!
Between the timing of the post ("just on the phone with"), reference to not writing books and originating from an IP address in Atlanta, Georgia, it was pretty clear who was the likely poster. If not Evans himself, most thought it could have been a LIGATT employee. As with any "case", circumstantial evidence isn't enough, so most people moved on with their own opinions of the incident. Riley wrote his own summary of the incident the day after it happened.
Steve Ragan from The Tech Herald wrote an article that mentioned the incident and brought new information to light. In a press release by LIGATT, Evans claimed that racism was the basis for a lot of negative attention he had been receiving. Evans told Ragan that during the Skype chat to set up the phone call, Riley had called Evans "the N-word". When asked for logs proving that claim, Evans said he didn't have them right there, and never managed to produce them for weeks after. In a subsequent interview, Ragan again pressed Evans for the logs to which he replied "that he had blocked Riley on Skype and the logs were unable to be recovered." This is curious given Evans and LIGATT's claim of being able to provide forensic services, even going so far as to provide such services to a city's government.
When Ragan asked Evans about the IP address in the blog post's comment section, Evans provided a billing statement showing he was a Megapath customer, stating that "we don't know who BellSouth is." Being a customer of one ISP does not prove you are not a customer of another ISP, as many companies use multiple providers for redundancy or based on regional availability.
Some time in July, an anonymous source sent information to Ragan providing additional information about the IP address that established a more positive link to LIGATT Security. By connecting to the IP on a specific port, the 2Wire device would provide a list of NAT connections and firewall "pinholes" (i.e., rules allowing specific traffic) without authentication. In the list were connections from an internal IP address (e.g., 192.168.x.x) to a machine that ran a web server redirecting traffic to ligattsecurity.com. The connections were to port 3306, most commonly used by MySQL databases. The service on port 3306 for that IP is not available to the Internet; it is restricted to people behind the firewall. This suggests that whoever owns that IP address has the ability to connect to internal LIGATT databases, while the rest of the world cannot.
With the evidence mounting up, all of the above is still not conclusive to some people. One could argue that something else runs on port 3306 or there is some exception for traffic where a non-LIGATT employee could connect. However, Ragan also shows that he received e-mail from Evans himself, that originated from that IP address too.
Gregory Evans can make excuses all day long, but eventually he must realize the evidence is there. Either he or another LIGATT employee lost their temper and reacted poorly to an incident that they perceived to be negative. Instead of hitting a wall, smashing a keyboard or watching skunk videos on YouTube, they posted an anger-laden comment threatening the life of Riley and his family. Perhaps Evans needs a refresher on U.S. law that outlines "[transmitting] any communication containing any threat to kidnap any person or any threat to injure the person of another" that is punishable by fines "under this title or imprisoned not more than five years, or both."