On June 27, 2011, The Hacker News posted a brief article demonstrating a Cross-site scripting (XSS) vulnerability in the EC-Council.org web site. Kristian Erik Hermansen has submitted XSS vulnerabilities in portal.eccouncil.org/forum/login_user.asp and portal.eccouncil.org/jobs/forgotpass.asp to </xssed>, a site that tracks XSS vulnerabilities on company websites.
Since the web site has an extensive member area that requires authentication to reach, XSS vulnerabilities are certainly a serious concern. Largely, they are also easy to protect against with relatively simple coding guidelines. This is the type of vulnerability any respected ethical hacker should be able to find.
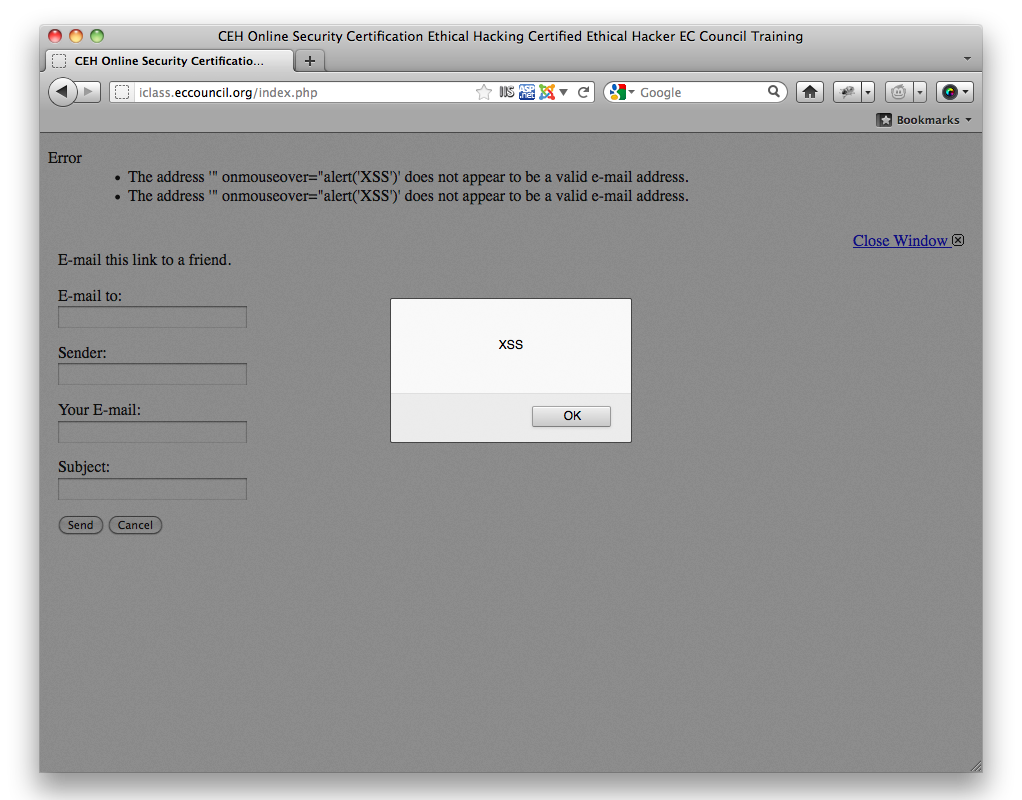
After recent actions of EC-Council became more public, we received a tip that the EC-Council.org web site is vulnerable to an additional XSS vulnerability. The iclass.eccouncil.org site appears to use the Joomla! CMS or a system similar to it. The 'com_mailto' component has several parameters vulnerable to XSS via POST requests. using FireFox 8 and the following injection string, our source demonstrated the vulnerability:
" onmouseover="alert('XSS')

Sep 30, 2012 Update: Ryan Dewhurst (@ethicalhack3r) points out that the vulnerability has still not been fixed, despite the vendor being aware of the issue for over six months.