It always amazes me how often and blatantly people will incriminate themselves. Even today, when most (or at least most dangerous) attackers are motivated by profit, there are still .script kiddies. that simply do it to make themselves seem cool among their peers. To meet this end, they have to brag, show off, and command respect in a way that runs completely counter to the usual desire to not get caught or exposed. Sooner or later, they show off to the wrong person.
This is the case with Yousif Yalda, a 17 year-old from Skokie, who has been in contact with me over the past several months. If the subset of security professionals on my Twitter feed are any indication, I'm one of many people in this field that he has been in touch with recently. Throughout this time period he has tried hire me for his web security and penetration testing business, VAPT Security and discussed, at length, his desire to make it big in the security industry. He also has quite a temper, which would flare up when I dismissed requests to work for him, refused to post comments to his blog, and criticized some of his work. This is when he would make allusions to his "black hat" past, terrorizing AOL with Visual Basic programs written by his friends (no, I'm not kidding).
I'm all for someone throwing their hat in the ring, and I also think it.s fine for someone to put their "black hat" past behind them, perhaps even using those experiences for the forces of good. I do, however, expect people like Yousif to conduct themselves professionally and not damage the image of penetration testers as a whole. Running assessments and attacks on sites without their permission, showing off confidential documents stolen from organizations, and attempting to infect others. PCs with trojans are not ethical activities for penetration testers to run outside of an agreed-to test.
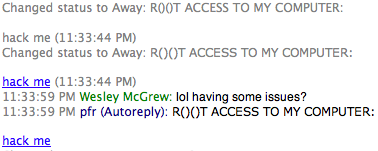
Going back to how people incriminate themselves, I wouldn't have found out the extent of Yousif's activities if he hadn't invited me to along to see, and if he didn't have such a desire to brag and demonstrate his (mostly imagined) skills. Previously, he had mentioned running scripts and tools against other sites, and admitted that he had not asked permission beforehand, but I had never seen any of it first-hand. Then one day I saw his away message set to this:

I just figured he had gotten owned. Copying and pasting the link showed it going to his IP address on 5800, which is typically a web interface to a VNC server. I didn't get a response on the AOL name when I asked if he was having problems, but then he showed up on gtalk:
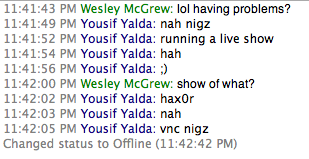
It was an invitation, not only to the people on his "buddy list", but also to anyone who could check his away message (basically anyone on AIM). I clicked, and was dropped into a VNC session (without mouse or keyboard control) watching Yousif Yalda "drive". Over the next few hours that night, Yousif was in a veritable script-kiddie zone. In an effort to impress another friend on his AIM buddy list, he went through several "hacks", past and present, of varying success. All this with the knowledge that who- knows-who-else was watching.
I took screenshots, and I've sat on them for a week or so now. I've decided that, since he doesn't show any remorse or regret for the things he's done, that at the very least his "targets" have a right to know who's been pointing crappy scripts and tools against them. Potential clients should know how little he respects ethical procedures and confidentiality. Others involved in security that he's been talking to (a seemingly large number) need to know who they're dealing with. At the very least, know when you're talking to him that there's likely to be someone else watching on a VNC session.
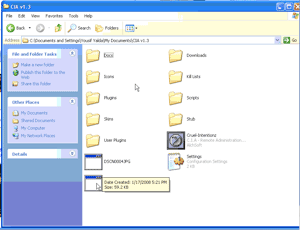
On to the fun part: a look into the mind and actions of a script kiddie. We'll start with an attempt to infect a friend with a trojan. Here he is making a copy of the server executable:
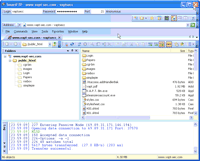
-and uploading it to the same hosting that he uses for his business:
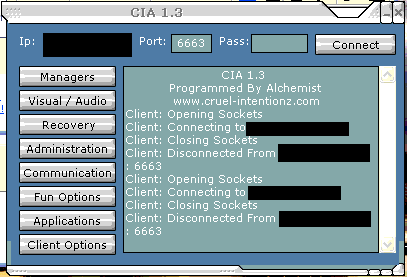
I'll spare you the logs of Yousif trying to convince his friend to download and run the trojan, which he disguised as the setup file for a Steam account. He managed to convince the victim after some time, and even got him to disable AV and firewalls, although unfortunately for Yousif, it appears that his victim was probably NAT'd behind a home router:
Despite its lack of success, it impressed Yousif's friend he was showing off to enough to ask about the "CIA" name. A habitual liar, Yousif claimed he made it "2-4 years ago." I have since found out that many things he will claim about his associations with others and things he has done have been greatly exaggerated (including claims that a well-known web security professional hacked sites alongside him).
Next Yousif showed his friend, and anyone else watching, a directory in which he keeps documents that he has apparently stolen from a real estate/mortgage company. There are many letters from banks about the status and balance of people.s accounts, taxes, and other personal information. I can't even really show screenshots here, even of the directory listing here, as I would have to censor them so heavily it wouldn't be worth looking at.
Here's a couple of emails he sent to himself from hacked accounts as trophies:
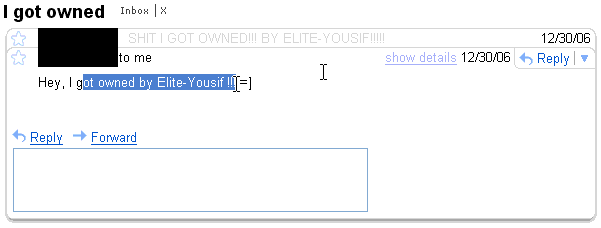
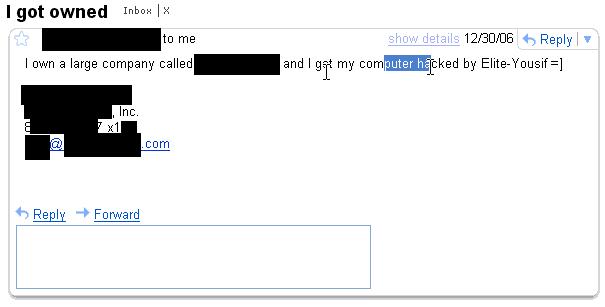
Those are pretty old, but then he decides to show off some of his scripts and tools on one of the old victims (the latter of the two victims above).
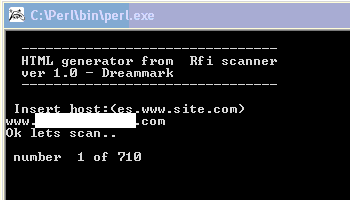
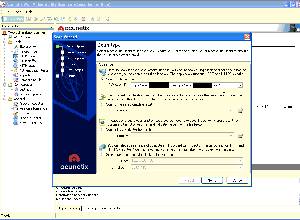
He really likes a perl script that he has for doing RFI scanning, and Acunetix, which you might remember from my last post as the tool he pointed at this website. Thankfully, in this case, he doesn't find much. Notice in the screenshot of Acunetix above that he accidentally pastes the URL to the current site he's scanning right after the URL of the last site he scanned with the tool, revealing yet another target besides myself and the sites he scanned during his open VNC session.
For the last example of Yousif Yalda's activities, we have him taking aim at a real estate investment firm that he has apparently been playing with for some time, judging from the dozens of entries in his browser history. As you can see, he doesn't quite understand what he needed to substitute into the script before running it:

The funny part of this is that when he does go to try the RFI out, he realizes that he needs to remote-include a php shell, so he goes and does a web search for r57. Instead of finding the source code hosted on another site, or setting one up himself, he manages to find another site that is already running r57 as a result of RFI or similar, and tries (without realizing what he.s looking at) to include the rendered page from there instead of the php source. It's a wonder that this guy has anything to show off to his friends at all, and one would hope he wouldn't stumble around so much on a real penetration test.
So what do we take away from this? Despite claims that attackers now are motivated by profit, we still see script kiddies (mostly in their teens) that are launching attacks in order to gain the admiration and respect of their peers. To this very moment it blows my mind that he invited me and others to watch this, and at first I wanted to ask, "If this is what Yousif does when he has invited people to watch him, who knows what he gets up to when he's on his own", but then I realized that he thrives on the attention and admiration. Although it's not the kind of attention that he wants, I hope that others in the security community (or even potential clients) that have been or will be in contact with him see this and realize who they are dealing with. His targets are also being notified so they can review their logs. While I thought about that for a while, I came to the conclusion that I normally notify other potential victims that I become aware of in any other kind of incident investigation, and these deserve no worse.
I have enough material on this to cover another dozen blog posts, and I might post a more lighthearted "deleted scenes" later on. If you have any interesting Yousif Yalda stories (which, if he's tracked you down to talk to you, you do), feel free to post them as comments or email them in.
I'll be back on a regular posting schedule with some book reviews, news commentary, and technical posts soon!