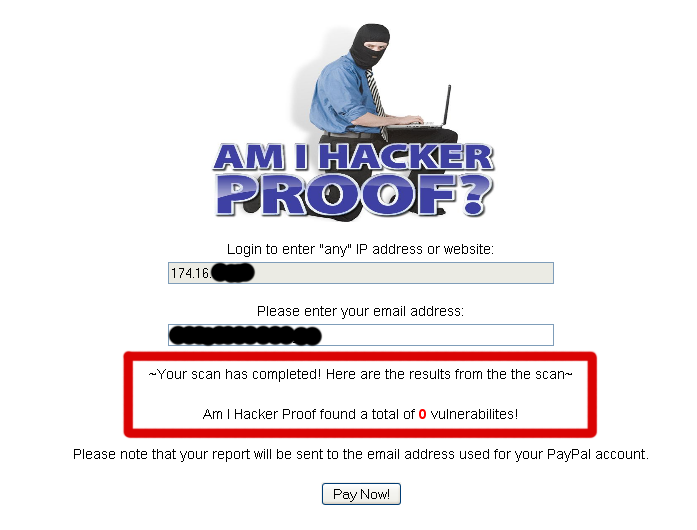
LIGATT and Gregory D. Evans have been running a site called "Am I Hacker Proof" since early 2010. The site purports to test your IP address for vulnerabilities to determine if your system is "hacker proof". Looking past the entirely laughable concept that any automated test could answer that question, the service offered by Evans is entirely unreliable and potentially violating the commercial software license of Rapid7.
After CNN failed to do due diligence, the news organization put Gregory Evans on the air and let him pitch his web site while offering "expert" analysis. Days later, Evans and LIGATT announced their site "had been the most used online security audit service this week". This was based on his claims that over 200,000 people used the service and a guess that no other scanning service performed that many scans. While we can only display a healthy dose of skepticism over this figure, we can say with certainty that every person who did use it may be at greater risk than before.
It is human nature, that when we are told we are "ok" or "doing good" at something, we often become more lax in the activity that led to such a comment. If the average person is told they have "no vulnerabilities" on their computer, then they will not worry about attacks. They may become more complacent and less likely to take safety precautions they did before. Worse, such a claim may cause them to overlook or disregard warnings that something is wrong, such as malware infection or a compromise. Evans' "Am I Hacker Proof" does exactly that, lulling visitors into a false sense of security.

With this report, a typical end user would believe their system is perfectly safe. In reality, due to Evans' inability to configure the software they use, these results are entirely inaccurate. When the amihackerproof.com scan ran, it did not find the web server listening on a different port than 80. Assuming that the 'Free Scan' used a default scan policy, it was re-enabled on port 80 and scanned again. The second time, amihackerproof.com did not test the web server at all. No matter what vulnerabilities might be present, it did not look for them. Running the same software that the web site uses, the results were clearly more interesting:
[Update: After this article was posted, half a dozen readers contacted us indicating that the service did not generate any incoming traffic to the IP they tested. The site appears to be giving out "0 vulnerabilities" to everyone, without testing. After several more mails from the community indicating the site was not scanning them, Attrition staff finally saw traffic to one server tested. It appears that the service is very unreliable and will give no indication if it fails to actually scan a system.]
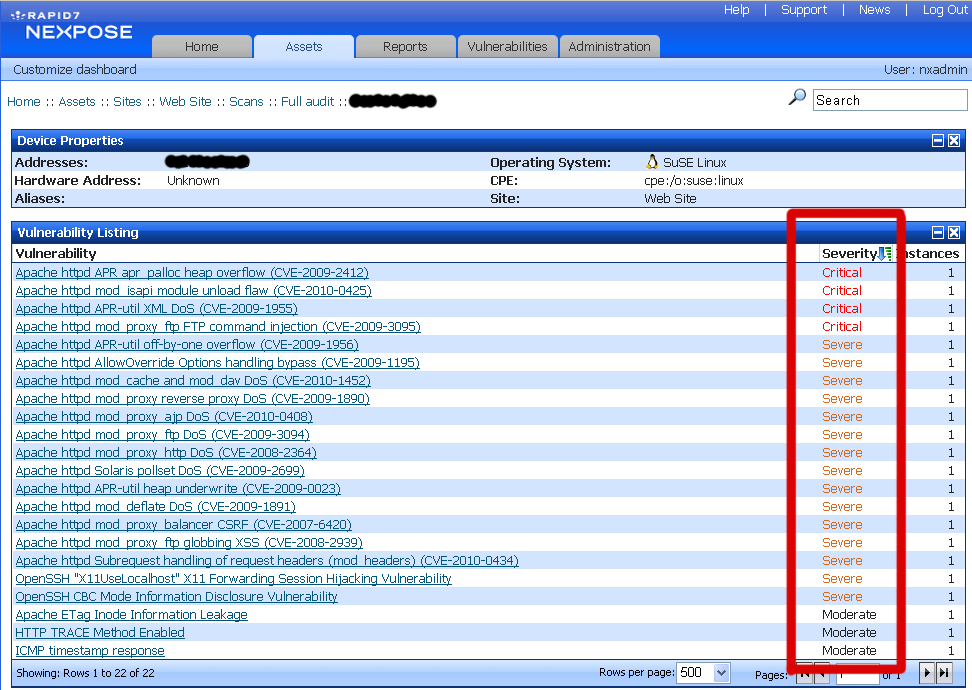
The software being used by "Am I Hacker Proof", according to the sample reports available, is Rapid7's NeXpose Vulnerability Scanner:

This is confirmed by examining the HTTP logs after a scan of this server. There are several instances of "rapid7", "r7" and "NeXpose" in the output.
This also brings up the question, is the scanning software they are using registered? According to one anonymous (but seemingly well informed) tip sent to the Errata team here, LIGATT uses a wide variety of software without the proper licensing. According to the Rapid7 licensing, using the free version of their software (i.e., the "Community Edition") is restricted to internal use and 32 IP addresses:

The free scan offered by "Am I Hacker Proof" gives a simple count of vulnerabilities found. To get additional information, you must pay for the LIGATT re-branded report based on NeXpose output. It is interesting to note that LIGATT charges up to $50.00 for the same report you can generate for free using the same software:
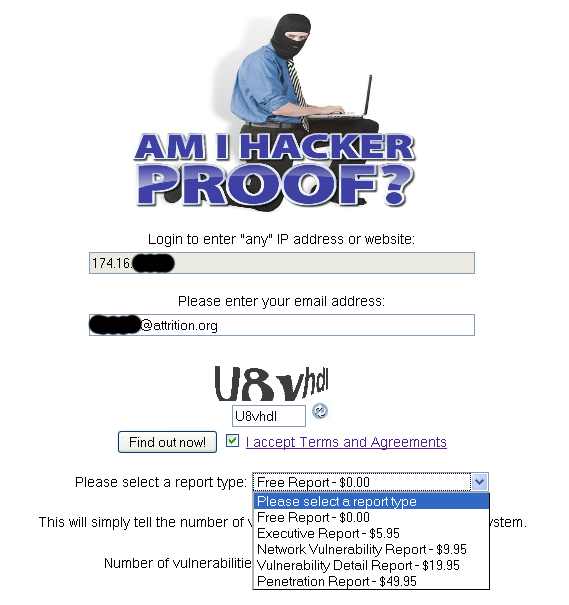
Scanning hundreds of thousands of systems (per LIGATT press release) and charging for the results demonstrates large-scale profitable violation of the Rapid7 license.
Attrition.org sincerely hopes that LIGATT is using a properly licensed copy of Rapid7's software.